Malicious Approvals
Malicious approvals let scammers drain your wallet. Learn to spot dangerous permissions and revoke them to secure your crypto.

What Is a Malicious Approval?
A malicious approval is a deceptive blockchain transaction that grants attackers permission to spend a user’s tokens without their knowledge. In ERC-20 tokens, the approve() function allows one address to control spending of another’s assets, a legitimate feature for DeFi interactions.
However, scammers disguise these dangerous permissions as harmless actions like wallet connection, airdrop claims, or platform verification, exploiting users’ trust and unfamiliarity with transaction details.
The widespread approval-based attacks that targeted Uniswap and other DeFi users in 2022, draining wallets of millions through disguised permission requests, really showed why understanding and managing approvals is crucial for Web3 safety.
How Malicious Approvals Work
Once signed, attackers use the transferFrom() function to drain approved tokens instantly or gradually over time, often waiting days or weeks to avoid immediate detection. These approvals persist on-chain until explicitly revoked, meaning victims remain vulnerable even after the initial interaction.
Phishing sites commonly embed malicious approvals within fake mints or drops, compromised DeFi interfaces, and social media campaigns. The blockchain honors whatever permissions users grant, making prevention the only effective defense since transactions cannot be reversed.
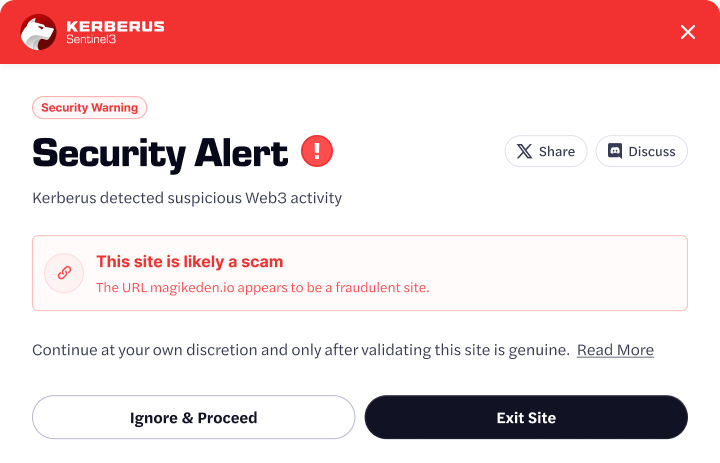
Use a top Web3 security tool like Kerberus to stop these attacks in real-time:
How to Reduce Risk
- Avoid granting unlimited allowances to unknown or unverified smart contracts, and always verify contract addresses against official documentation
- Use approval management tools like Revoke.cash to regularly audit and revoke outdated permissions across all networks
- Employ transaction simulation services that preview approval effects before signing, showing exactly what permissions are being granted
- Maintain minimal token balances in wallets used for experimental or high-risk interactions
Written by:
Werner Vermaak is a Web3 author and crypto journalist with a strong interest in cybersecurity, DeFi, and emerging blockchain infrastructure. With more than eight years of industry experience creating over 1000 educational articles for leading Web3 teams, he produces clear, accurate, and actionable organic material for crypto users.
- •8+ years in crypto & blockchain journalism
- •1000+ educational articles for leading Web3 teams
- •Former content lead at CoinMarketCap, Bybit, OKX
Related Terms
See more glossary termsInstall once & immediately get protected from scams, phishing and hacks. Zero losses for 250k+ users in 3 years. Now with up to $30,000 in coverage.